The Unexpected Email
Podcast: Play in new window | Download
Subscribe: RSS
Episode 22: The Unexpected Email
Imagine receiving an email unexpectedly from yourself. You’d probably think that was pretty weird but you open it anyway and what you read next is even more shocking.
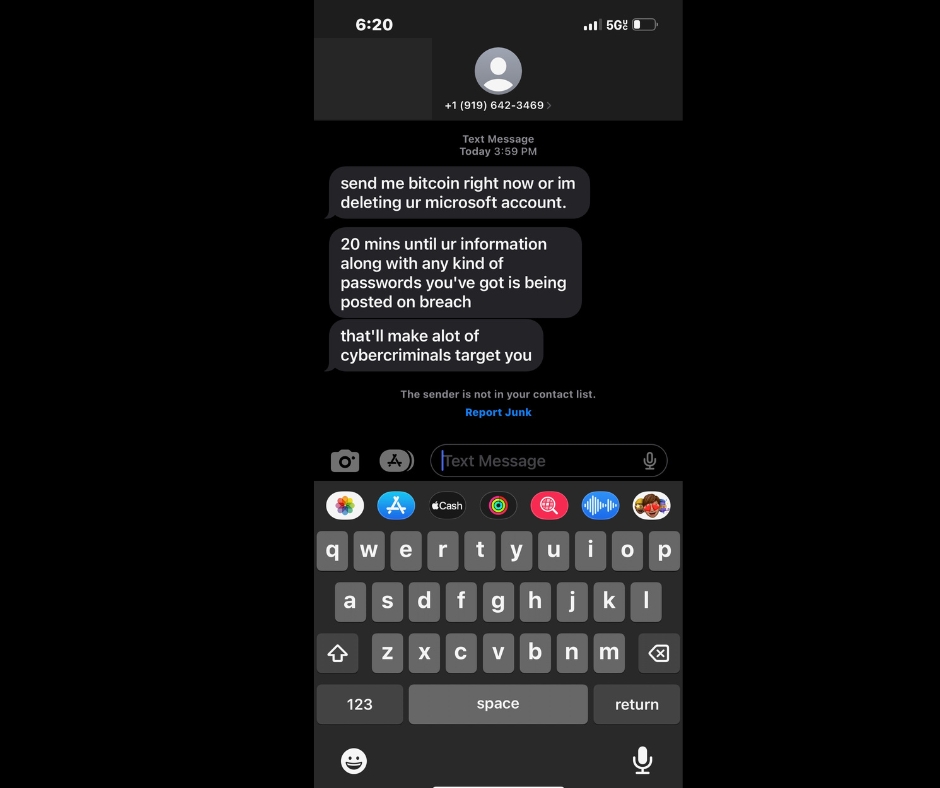
Someone else has access to your email and they want a ransom in bitcoin to return your email to you, and to not put all of the information found in your email on the web.
But that’s just the start of the story. It gets worse.
Transcript
People are the weakest link in any cybersecurity plan. We’re distracted, exhausted and often unmotivated. It’s time to change the approach used to protect our businesses, technology, identity and data. The human element has to be front and center in the war against data breaches and ransomware attacks. It’s time to educate.
When I was a senior in high school yearbooks were handed out as traditionally done every year, every senior year for most high schools. And actually, they’ve done for a lot of different grades in college. I think my kids have gotten it and every year they’ve been in school. But we only got him when we were seniors in high school. And we would get him signed by our friends and be messages, you know, great, great knowing you and good luck in the future and so forth. But there were a group of kids who would sneak sign yearbooks they would take people’s yearbooks, unsuspectingly and this happened to me. I had some students sign my yearbook that I never even asked to sign my yearbook was pretty cool to think about it. At the time. It was like God, it’s awesome. So and So sign my yearbook. I didn’t expect that didn’t know he was even even had my yearbook at any point. And I thought that was pretty cool. So this became a tradition in school where students would sign your books, unbeknownst to the owner of the yearbook. Sometimes it was great. Sometimes it wasn’t so great because they would write something inappropriate or mean because they didn’t like the student. But it was always unknown to the student or the owner of the yearbook that these students were signing these yearbooks. So it was sort of like they were hacking near your book signing new yearbooks. I don’t know if this tradition carries on today, at least not for your books he carries on in other ways. And we’re going to talk about that in today’s podcast. Welcome to the human element podcast, visit our website at the human element dotnet. For more content to help you strengthen your awareness of the people problem in cybersecurity. I am Scott Gombar, owner and Washtech, a client focused, security minded proactive IT service provider. Welcome to Episode 22 of the human element podcast, this episode titled, The unexpected email. So this one is a recent event that occurred to a sort of client of mine, it was a referral from an existing client. And so I’m going to be a little vague as to some of the details are going to be vague, but I’m going to explained what happened to this person, and some of the mistakes that were made along the way. And what you should know what you should be looking out for. So I’m going to start first with saying this is a person in the financial world. And that’s as detailed as I can get with that. And then we’re using an email account, a free email account. So those services like Gmail, Yahoo, Outlook, Hotmail, sure, I’m leaving a few out. But services like that, where you don’t have to pay a monthly fee to use their email services, you’re going to see a bunch of ads within email and so forth. And they’re in the financial world. And the account was compromised. So we’ll just say like that. Now, I don’t know how the account was compromised, because we were not able to recover the account. And how it happened was the end user of the account suddenly received an email one day, and I’ll have a couple of screenshots that I have in the show notes, but they received an email from themselves demanding a ransom in Bitcoin, so it wasn’t a lot. It was a few $100. But then the hacker wanted the payment of a few $100 in Bitcoin. And, naturally, as I’m sure most of us would, the the end user panicked and asked around for some help and eventually got to me. So they contacted me, and at first I thought, because it was on a Sunday evening and typically my clients are not working and so I don’t usually get texts, or calls about any issues. But I did and figured out pretty quickly that it was a legitimate person. And they were they were of course panicked that their email account was compromised. He received an email from him from himself and it was demanding for several $100 in Bitcoin did the smart thing not paying the ransom because there’s no guarantee that if you pay the ransom, they will give the account back. And even if they do, likely, they’ve already stolen whatever’s in the email account, including your contacts. And that’s where this becomes a problem for everybody else, so your email gets compromised. And they now have access to all your contacts. So he didn’t pay the ransom demand. And this is just the beginning. So he was able to tried to reset the password. He tried to he tried to reset the password. And then when he couldn’t, that’s when he reached out to me. And I went through some Microsoft channels after speaking with him getting more details in determining that the password had already been changed. And it wasn’t anything he could do. From that perspective. We went through Microsoft channels, and Microsoft through Microsoft channels, we were able to this was an Outlook email, we were able to get to a reset screen where it had his phone number. I could see the last two digits of his phone number. And so I tried to reset password and wanted to send a text message you know, it was it said it would send a text message to his phone number. And I’m still talking with him and solemn to expect a text message from Microsoft. He didn’t get the I’m sorry, the system said that he had already tried this too many times there was a you can only try two times within a day. So we talked, we decided we’re going to wait till the next morning. Next morning comes I wake up Monday morning. So it was pretty early. I wake up and he’s I’ve already got a text message from him saying that he’s already reset the password and canceled the account. But received a message that said his account would remain open until I think for one month it was
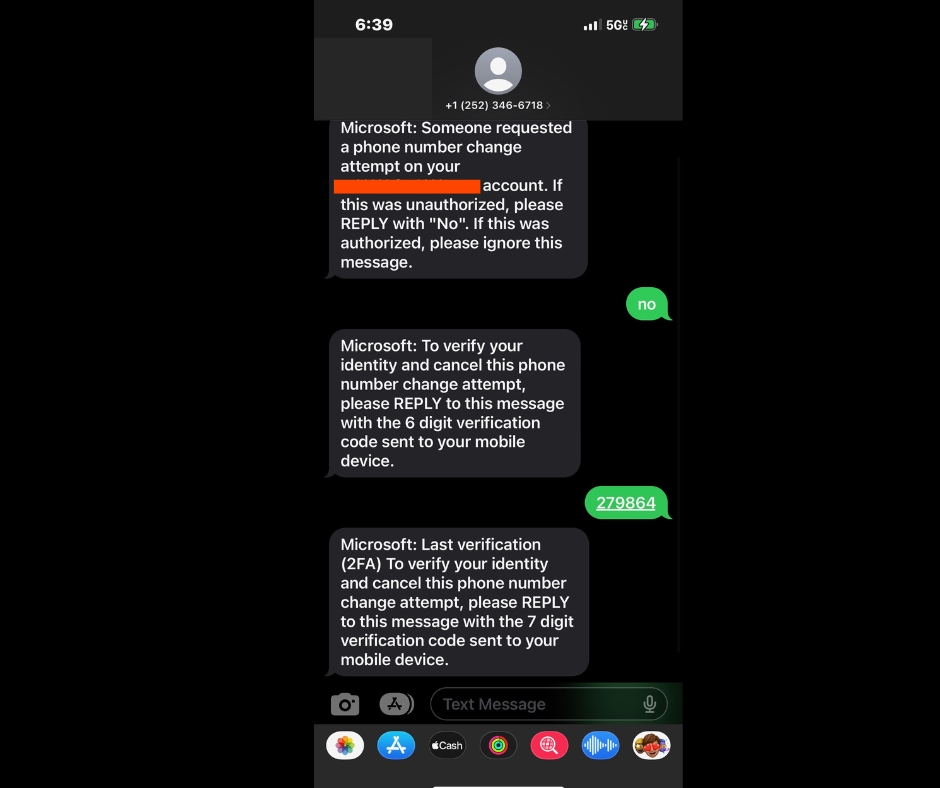
that concern me a little bit. But he then later received a text message purportedly from Microsoft saying did you request for your phone number to be changed on the account? And he of course said no, because he did not request this. So of course, he replies No, and gets an another message saying saying it’s from Microsoft to verify your identity. And cancel this phone number change attempt please reply to this message with the six digit verification code sent to your mobile device. And of course, he got a six digit verification code to his mobile device from Microsoft. The problem is this text message didn’t come from Microsoft. The problem is this text message came from
from the scammers who tricked him into supplying a two factor authentication code so that they could change the phone number. So they were trying to change the phone number. Microsoft was asking for the two factor authentication code, they send this message to him pretending to be Microsoft to trick him into giving them the code. So he gave up the code and now they’ve changed the phone number in the account. So now he’s lost all access to this account. And no way to get back in because now his phone number has been removed. So what you see here is the scammers slash fishers, slash hackers, cyber criminals, they’re cyber criminals, let’s call them what they are. They’re criminals that work over the web. They found a way into his email account. And no way for me to know how they did this because he doesn’t know how it started, whether it was a weak password, and they just were able to log in, or they fished them. Which would be my guess is they fished him somehow. Or, you know, some other methods somebody that knows him. So now he’s accepted that he’s lost the account, and he’s gonna have to move on from this account. And so I’ve given him some tips again. I just screamed from toe to toe, I can no longer scream at you if you’re in business, no matter what your business is in some more so than others. But if you’re in business should not be using a free email account. You should have an email account at your domain. So whatever your website is my website.com You should have my name at my website.com It should be that way. That’s for starters. Just From the professionalism, perspective, just for that reason, but on top of that, you set that up and you go through, hopefully Microsoft, but Daraa, other services, Google, and other services out there that you could also use. And they’re going to give you a little bit more security, because now you’re paying for a subscription and the subscription is, is minimal. It’s not that expensive. When you when you compare it to the other costs in your business, an email account is not that expensive. Now, here’s where the real problem comes in. So now he’s been hacked, breached for, I’ll use the word breached. compromised, is another good word twice on the same account. So that got him, they got into his email account, still no idea how. And they got him to give up multifactor authentication. So we hear all the time that multi factor authentication prevents 99% of email compromises and other account compromises. And that’s, I don’t know if that’s an accurate number. That’s what we hear. And the reason it works is because unless you fall for something like this, the human piece of it, they’re not really going to be able to figure out or they clone your phone, they’re not going to be able to figure out that’s called sim jacking. By the way, when they clone your phone. They’re not going to get past your multifactor authentication. But this is happening more and more, and I’m getting more savvy, every time I see these things, they’re just sending text messages that are very believable. And if you’re in the middle of a crisis with something that’s already way weighed heavy on you, and you’re bogged down with it, and you’re trying to resolve it, and then you get these text messages. So you’re thinking this might be the relief I need. And of course, it’s not, they’ve got you again. So that emotion, the emotion was there that he felt scared, embarrassed, concerned, for his clients, contacts that are in his email account. And we’re gonna get to that in a moment. A lot of strong emotion there. So when you feel in this way, it’s easier to make bad decisions, and to make rash decisions to decide that maybe this is the right thing to do. Or maybe this is some sort of relief coming from the people that I’m expecting support from or something along those lines and and a hook, it worked hook line and sinker, pun intended their fishing, get it? So now, the issue is I told them? Do you have a list of the contacts that you had in his email account? And he said he did. So that’s a good thing. So now he can inform all of these contacts, whether they’re clients or not contacts that his email account was compromised in more than likely the people that compromised his email account are going to try to compromise everybody in his contact list. They’re going to pretend to be him and send emails. And so now he’s got to deal with that follow up. This is borderline data breach. I don’t know the number of contacts, I don’t know. And, and I did advise him of all this, but I don’t know the number of contacts. I don’t know if they were clients or not. I don’t know what data was in, in this email account. This is borderline a data breach. And if this is depending on what state you’re in, in the United States, or if, if you’re in Europe, this could be considered a data breach. And so now it’s reportable, you have to report it. If you’re in certain states in the United States, you have to report it. If you’re in Europe, you have to report it. It also depends on a number of context. So there’s variables there but still questionable. And Eve even if you don’t have to report it, the right thing to do is to let all of your contacts know that you’ve been compromised, your email is compromised, they can expect to get something from your email account that is not really you. And I’ve seen this time and time again over the years where somebody’s email account gets compromised, and it used to be that the email account would try to spend a try to spread a Trojan horse through the compromised email account. As the way it used to be Trojan horse being, what it sounds like, if you’re familiar with the story about the Trojan horse, basically, a gift was delivered look like a gift. And it was really filled with soldiers who bring it inside the city walls and the soldiers in the middle of the night come out of this giant wooden horse and attack the city. And because of this, because they tricked them into believing it was a gift and believing that it was safe. While everybody was sleeping, they ransacked the city. Well, that’s what a Trojan horse virus does, makes you think it’s something else, you know, they might get a an email saying, hey, check out this cool new application, it’ll help you with streaming videos. And so they install it and not doesn’t really do what they say it’s going to do. It’s, it’s a Trojan horse, and now it’s doing other things in the background, you may not even notice that it’s doing those things, your computer may just now be a a bot for a bigger, much larger attack. The human element played a big factor in this particular email compromise, most likely initially started with a phishing attack, that could that tricked him into going to what looked like a Microsoft page and logging in. And then because the attackers realized he had a phone number, an account that was getting two factor authentication to text message, he then which by the way, is a good reason not to use text message for two factor authentication. If you can avoid it. It’s better than nothing. But it’s not better than an app or a YubiKey or something like that. So he fell for the phishing email, most likely, he definitely fell for phishing texts that tricked him into giving up his two factor authentication for Microsoft. And all of this happened within maybe 24 to 36 hours. They move fast, they’re very sophisticated. Now, they will send very convincing text messages and emails, they will try to extort you, they will try to threaten you, they will try to do all kinds of different things. And I’m, if I’m not mistaken, he did receive a threat of sorts. I believe something along the lines of we’re going to tell everyone that your Oh no, we’re going to post your information on the internet, I think is what they said. The conversation with the with the hacker was a little a little vague, and not a little vague. It was a little, I guess some parts were vague. Clearly was not English was not their, their primary language. And whether they were using a translator or not, I’m not sure. But it was clear that English was not the primary language. And so somebody in another country compromised this account. Now I do believe if he had reached out to Microsoft support, and said, Listen, my account was compromised.
And they can see where he typically logs in. And hopefully help them with that. If it’s you know, suddenly they see logins and just gonna throw a country out to let’s say, China. They know though he’s never been to China. And typically he logs in and in the United States, in certain geographical areas, this should be able to help them with that. However, Microsoft is not usually very helpful with those things, unfortunately. But you can see how easy this is. This is not this is a business owner. This is someone who has a high level of energy education works a lot. And maybe that played a role in to him falling for the initial compromise. And he fell for the scam he fell for of potentially a phishing email and he fell for the text message scam, getting his two factor authentication code. It is that easy. And that fast and they move fast. Once they’ve got once they got the hooks in you, they’re going to reel you in and they’re going to finish you off. They’re going to take care of whatever they need to take care of. And now you can I can guarantee you that they’re going to do the same to all of you or they’re going to attempt to do the same to all of his contacts. So if he’s one of them, great, because that gives them a heads up to expect us to be coming down the pipe. And now he doesn’t know at least he’s got that off his conscience. If you did warn them. But warning doesn’t always suffice. You know, I talked to different business owners Was that are, you know, they have different compliance needs and so forth. So let’s just use the financial advisor as the example. This was not a financial adviser. They’re just in the financial world. But I’m going to use the financial advisor in this scenario. And matter of fact, let me use a tax preparer. So you use a tax preparer. And, you know, a tax preparer typically has to get documents from the person to prepare the taxes for and will tell them do not send sensitive information via email. It needs to be encrypted, if you’re going to send it to me, most average consumer isn’t going to encrypt an email, doesn’t know how to encrypt an email, and isn’t going to waste their time trying to figure it out. And then they will tell the tax preparer will say do not send social security numbers or other sensitive driver’s license numbers, things like that in an email. And they will do it. Almost always, I hear it every year. Yes, I got social security numbers in my email, I got driver’s license numbers in my email, I got sensitive tax information in my email, tax IDs, whatever it might be, all the time, no matter how many times they tell their clients don’t do it, the clients do it. So there’s a reason why those messages, you know, you have those disclaimers at the bottom of the email that says if this isn’t intended, if you’re not the intended audience, please delete. But also the people are putting in more now saying these are these are the ways we we handled this this type of transaction. So for example, I, I know of real estate closing attorneys, they will now say, to verify the wiring instructions for the closing fees, please call our office, and then you know the phone number, because it happens in the real estate world a lot where those email conversations are compromised. And then wiring instructions are sent to the to the buyer or the seller. And there’s an a fake wiring instructions. So they end up sending 10s of 1000s of dollars to someone else. Never Never, that money never gets seen again. So now just imagine for a minute that this email came from your realtor or your real estate attorney. And they told you to change the wiring instructions and send the money to a different account. And but it came from their email address. So now you think okay, I could trust this. And this is why now a lot of a lot of real estate attorneys and realist realtors are now including a, a default message in your email that says to verify wiring instructions, call XYZ before making the transaction. So this is the problem. Now there’s a bunch of contacts within this email account that are going to get emails from someone that they believe to be their actual insurance person. Or find a financial person, sorry, financial person, but insurance, it’s all the same financial insurance, real estate, any of these industries health care, they’re all the same. If they if the account is compromised, now there’s a certain level of trust because it’s coming from that email account that you’ve contacted, you’ve exchanged emails with before that level of trust is there. And more than likely more people are going to get scammed. And more and more people are going to lose money and moves lose out on potentially sensitive data. And just a lot could go wrong here. That’s why it’s important. So to recap, importance, you have to have a strong password, you should have some, at least some form of two factor authentication. And in this case they did. But you also need a level of awareness to say, This isn’t right. Microsoft doesn’t proactively text people like this. Or you know, again, I don’t know how they fell for the phishing scam. But understand you shouldn’t be clicking links, in email from unsolicited emails. And you shouldn’t be downloading things from if you did download something, you probably are in worse shape than you realize. But all of these things need to be considered before even making the decision to review an email. And services like Microsoft and Google are great at catching a lot of this stuff. But they don’t catch everything. And sometimes they’re behind. So with the in the case of Google, even with Google workspace, they sometimes will let any email through into your inbox and a few hours later, you’ll get an email from them saying we’ve detected a phishing email. I just saw this today as I’m recording this for one of my clients, so it does happen. You cannot rely on these services alone. You have to rely on your own intuition, your own awareness that these things are happening. And it is, it is a battle and it’s going to get tougher with artificial intelligence, it’s going to get tougher with deep fakes, it’s going to get a lot harder. So that’s why that’s why I’ve created this, this podcast in hopes to help educate people and to prevent these these types of things from happening. So that’s gonna wrap it up for this week. Hopefully this helps someone stay out of trouble with email. Until next time, stay secure.




 The Human Element
The Human Element
Leave a Reply
Want to join the discussion?Feel free to contribute!